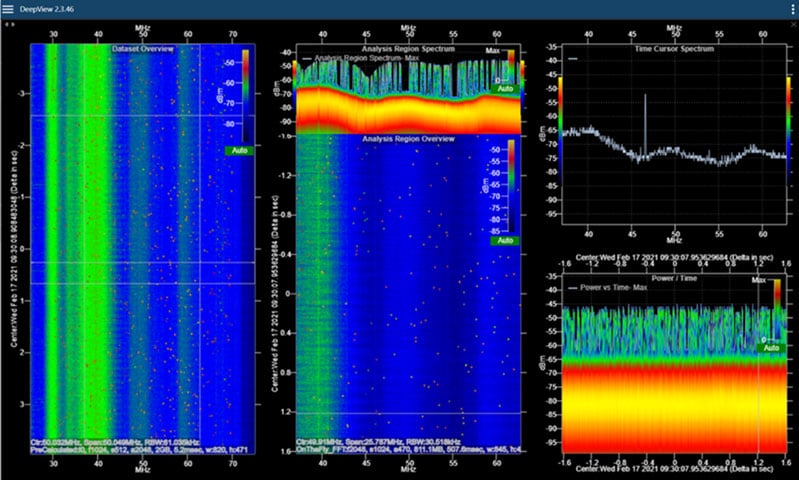
Deep Signal Capture – Spectrum Dominance & the US Army Field Manual 3-0 Operations

Part 3
In part 1 and part 2 of our series, we looked at the new US Army Field Manual 3-0 “Operations” and how units must “account for constant enemy observation,” observation, which includes electronic surveillance and SIGINT. We looked at Tactical EMCON and Evading Enemy Geolocation risks and highlighted the CRFS solutions that help to mitigate the risks by providing enhanced realistic training. In this final part, we look at the Deep Signal Capture risk group, how forensic analysis of the RF signals could deliver intelligence to the enemy, and how the threats can be replicated in training to learn and counter.
Read the reference here.
Para 3-65. Because Army forces employ an increasing number of capabilities that emit electromagnetic radiation that enemies can target, leaders must apply emission control measures, balancing the risks to the force with the risks to the mission. As risk to the force increases, leaders increase their emission control measures. There may be times that the risk of friendly emissions being detected and targeted is assessed as too high, causing Army forces to use methods of communications with no electromagnetic signature…
Read the reference here.
Deep Signal Capture Risk Group
Below are three FM 3-0 identified risks grouped together around evading Deep Signal Capture. This refers to the ability to capture the IQ data of a friendly signal, quickly analyze it, and then produce actionable data. The data can then be used to assess the effectiveness of the troops’ ability to evade detection. This could include creating signal detectors, decoding, or simply understanding the US Army’s electromagnetic baselines. These risks are specifically important for special operations forces, cavalry scouts, and other forward reconnaissance forces operating near enemy SIGINT forces.
Using data-burst transmissions
Burst transmissions involve compressing the data and broadcasting at a high data signaling rate over a short time period in an effort to evade detection by the enemy. To correctly determine the effectiveness of this method, it needs to be tested in the field. The CRFS SenS Portable or Sens Remote RF recorders can record large amounts I/Q data over a prolonged period. The data can be analyzed using the Deepview software to look for burst transmissions allowing CEMA/OPFOR Instructors to create custom detectors within the RFeye Site software. Once created, then detector-based TDOA automatically can try to detect and geolocate friendly burst transmissions. This capability simulates the enemy SIGINT library building process right in front of troops, opening their eyes to how easy (or hard) it is to detect their transmissions (including encrypted burst, LPI/LPD transmissions, and frequency hopping signals). This is also a great capability for Special Forces that are looking to operate deep behind enemy lines and shore up their EMCON.
Masking emissions using terrain and manmade structures
To remain undetected but still be able to communicate, troops can use natural features such as mountains or valleys to shield their transmission or in urban areas buildings can perform a similar function. To test whether terrain or buildings are successfully masking transmissions, the simulation functionality in RFeye Site can be used. Site software incorporates terrain mapping and structures into its RF simulation functions with the option for bespoke Lidar data to be loaded in. This can give troops a good idea of their transmission options before they deploy. In training emission masking can be tested in a live scenario. Using the CRFS geolocation capabilities, instructors can attempt to locate the communication teams practicing terrain masking techniques. Soldiers can take note which material, structures, and natural terrain works best with each radio system and then apply it into Tactics, Techniques, and Procedures (TTPs). Practice in the garrison, to be ready for the field.
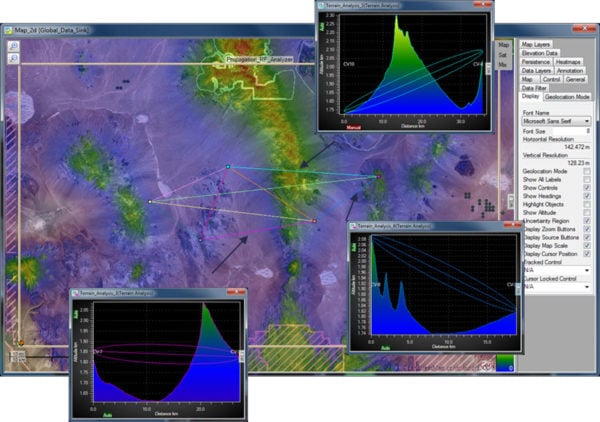
Terrain analysis inside Site software highlights the impacts of the physical environment to line-of-sight communications.
TDOA coverage when Nodes placed in a Valley (left), versus when placed on mountain peaks (right). Red highlights where all three Nodes can view signal. Simulation conducted inside Site Software. Soldiers can use CRFS modelling to uncover possible locations where terrain provides a safe zone from transmissions, without the threat of geolocation.
Employing deceptive emitters
Deceptive emitters can be employed to confuse the enemy into thinking an RF emission is coming from a real piece of equipment. This could be anything from radio transmissions to radar systems. When deploying deceptive devices, it is important to capture the Measure of Performance and Effectiveness (MOP/MOE) of these fake transmissions. Information Operations planners must answer the question, “did the enemy take the bait?” and “How do these deceptive devices compare to real communications?” SenS Portable and Remote, using DeepView signal analysis software allows Information Operations professionals to observe 100% of signal transmissions within 100MHz instantaneous bandwidth (IQ data) from 9kHz to 40GHz. IQ Data from SenS Remote/portable can then be exfiltrated in various formats to MATLAB and other third-party software for replay.
Conclusion
However hard troops try to disguise their electromagnetic signal, whether by using advances in technology, natural features, and terrain or by deception, there will be people on the other side trying just as hard to detect and geolocate them. By testing and evaluating TTPs on the training ground, troops will have more confidence that the methods they are employing will be effective. This can be achieved by installing a network of CRFS receivers in and around military training grounds. Signals can be detected, geolocated, and recorded so that troops can experiment with different methods and learn in a realistic training environment. Our solutions are TRL9 and easily procured through multiple DOD contracting pathways, both CONUS and OCONUS.
Zac George
Zac George is the International Business Development Manager for CRFS. He is a former naval Electronic Warfare officer and also has experience in digital decoding. He speaks regularly on EW and spectrum topics globally, and lives in Switzerland.