
A fully functioning radar provides crucial situational awareness in a wide variety of military settings. And as a key component in the electronic warfare arsenal, it is likely to be the target of countermeasures by opposing forces designed to degrade friendly capabilities, most likely some variety of radar jamming. This can range from straightforward brute-force jamming attempts, where an overwhelmingly powerful wideband RF signal is used to drown out the subtle return signals from objects, to a more targeted approach where the jamming signal is frequency-matched to the radar operating frequency, right through to sophisticated radar spoofing, where fake return signals are generated, purporting to show objects in locations where they are not, in fact, located.
Radar Jamming
So what form do these countermeasures take? If a radar operates on a single frequency, and this frequency is known, then all of the jammer’s power can be concentrated at this frequency – so-called spot jamming. If the frequency is not known, or if the radar uses some form of frequency hopping, then the jammer needs to target multiple frequencies or a band of frequencies – this technique is known as barrage jamming. The jamming signal will almost always be of lower power than in the spot jamming case, as the power is spread across the frequency range. A third jamming format, sweep jamming, forms a compromise between the previous two by employing its full power at a single frequency instantaneously, but rapidly sweeping that frequency through a wide frequency range.
To work out whether jamming will be effective, we need to consider the jamming-to-signal ratio (often denoted as J/S or JSR). Very roughly speaking, jamming will be successful if the jamming signal is much stronger than the return signal from an object. The power of the jamming signal received at the radar will depend on the initial power of the jamming signal, and on the distance between the jammer and the radar. The power of the return signal will depend on the initial power of the radar signal, the radar cross-section of the object, and the distance between the radar and the object. In real environments, additional factors such as weather conditions, terrain and line of sight to the radar also affect jamming capabilities.
Radar Spoofing
Radar spoofing exploits the fact that radar determines the distance to objects by measuring how long it takes the signal to return to the radar. If an adversary can change how long this takes (or more accurately, how long it appears to take), the radar can be deceived into showing objects in positions that they are not actually in. So how can this be done? The simplest way is to record incoming radar pulses, and then play them back with a slight delay. The round-trip time will appear longer, and the object further away. It is also possible to replay the pulse multiple times, meaning the radar will display multiple objects at different distances along the same path, making it difficult to impossible to pick out the true location. More advanced spoofing systems can also change the frequency of the signal when playing it back, allowing them to mislead Doppler radars, which use the change in frequency of the return signal to determine how quickly an object is traveling.
Jamming Countermeasures: LPI Radar
What countermeasures are available to deal with the threat of radar jammers? One approach to avoiding being jammed is to prevent enemy forces from knowing that you are using a radar in the first place. This is why low probability of intercept (LPI) radars were developed. They seek to evade detection by deploying a range of features, including frequency hopping, power management techniques and advanced scan patterns/modulations. These modulation types include frequency-modulated continuous-wave (FMCW), phase-shift keying (PSK) and frequency-shift keying (FSK).
FMCW radars transmit signals at a steadily varying frequency, most often a triangular waveform modulation as seen below.
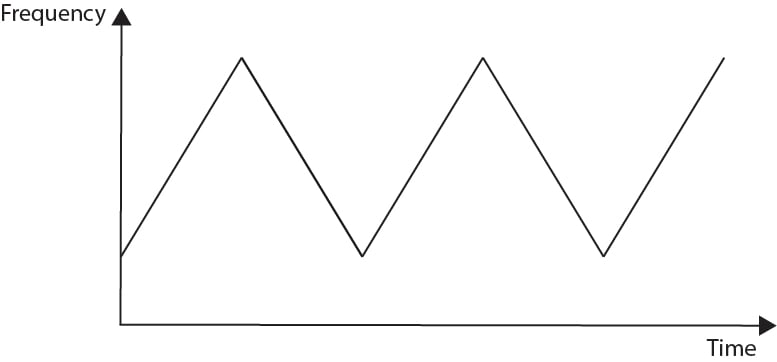
FSK radars transmit signals at a set of discrete frequencies, hopping between those frequencies according to a predetermined pattern. This pattern appears random to adversaries, making it much harder to intercept/pick out from the noise. In addition, any jamming attempt would need to be able to follow the frequency changes in real time.
PSK radars are somewhat similar, but use shifts in the phase of the transmitted signal to encode information, allowing the return signals to be picked out from the background noise more easily. This allows the transmitted signals to be of lower power than would otherwise be necessary, making them much more difficult to intercept.
However, given a sufficiently long period of monitoring with a sufficiently sensitive receiver, even LPI radars can be detected. And once the signals have been detected and analyzed, jamming waveforms can be matched to the particular modulation type.
Jamming Countermeasures: Determining Jammer Location
If even LPI radars can be detected and jammed, then another jamming countermeasure will be required. This is where CRFS’s RFeye system comes into its own. Jamming signals are, by definition, powerful RF signals, which means they can be traced back to their source using RF geolocation techniques. The appropriate technique for doing so will be dependent on the nature of the jamming signal: wideband signals, such as those associated with barrage jamming, can be located using time difference of arrival (TDOA) techniques, where a network of three or more receivers use the differences in the time that they receive the signal to pinpoint the location of its source. Meanwhile, narrowband, spot-jamming signals are best located using an angle of arrival (AoA) approach, where two or more receivers use the angle of incoming signals to determine lines of bearing to the signal source. RFeye Arrays offer the flexibility to employ either mode of detection, depending on your tactical requirements. With an operating frequency range from 20MHz to 18GHz, almost all jammer signals will be detectable, even frequency hoppers. And with RFeye’s 3D TDOA capability, even jammers mounted in aircraft can be detected and geolocated. Once the location of the jammer has been determined, then measures to neutralize it can be undertaken. RFeye receivers will also provide detailed information about the nature of the jammer signals, allowing friendly forces to adjust their use of radar to protect against future jamming attempts.
Find Out More
If you would like to know more about how RFeye can be used to help protect against the threat of jamming, then get in touch with us here at CRFS, and a member of our team will be happy to help.
%20CTA%20cover.png)
Brochure
RFeye Node Overview
Discover our advanced superheterodyne RF technology for superior sensitivity, frequency stability, and selectivity. Compare Node specifications, view the new RFeye Node models, and discover what makes them unique.
